Attackers use social engineering to exploit trust. An end user is more likely to open a malicious attachment or click a link if it appears to come from a trusted source. Your email client (e.g. Outlook, Thunderbird) maintains a "trust map" in the form of a contact database, aka address book.
Microsoft Outlook provides the Personal Address Book, Suggested Contacts and in Exchange environments, the Global Address List (GAL). The GAL typically holds contact information for employees, business partners, external contacts and distribution groups.
The Cryptolocker sample discussed on the Heimdal Security Blog piqued our interest, particularly the observations relating to theft of address book content. Our analysis focused on code paths that interact with Microsoft Outlook and the Windows Address Book. Let's take a closer look.
Sample information:
MD5: 9800562e50cbe9afa1b8d4f9a84eb089
SHA1: bba4d156b630ff4d7333f572b0d7fb034af2c10f
SHA256: 30ef75ebbbc7c27500dcbbf1db1aaab35be6a8e72e60a7a0ca91a621e4f62e6a
Compilation: 2007-08-28 11:12:19
Size: 661022 Bytes
Type: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
Following execution and a common "spawn, inject, resume, terminate" prolog, a second instance of Windows Explorer is launched:
Harvesting of Outlook contacts is performed using MAPI via COM, starting with calls to MAPIInitialize and MAPILogonEx. The call to MAPILogonEx will silently fail if Outlook isn't running at the time, since the profile name and password arguments are both set to NULL. If this happens, the harvesting thread will sleep for 3 seconds and try again, repeating indefinitely. Cryptolocker does not use (or need) valid credentials, since it can piggyback on the shared session established by Outlook on behalf of the logged-on user.
Once the call to MAPILogonEx succeeds, execution continues along the following path:
• IMAPISession::OpenAddressBook - returns containers for all address books in the user's profile. In an Exchange environment, this typically means Contacts, Suggested Contacts and the Global Address List.
• IAddrBook::GetSearchPath - returns a list of entry identifiers. This list contains the PR_ENTRYID tag, which is used to open and search each address book.
• IAddrBook::OpenEntry - opens the specified address book.
• IABContainer::GetContentsTable - returns the contents table of the address book.
• IMAPITable::GetRowCount - returns the total number of entries.
• IMAPITable::QueryRows - returns address book entries.
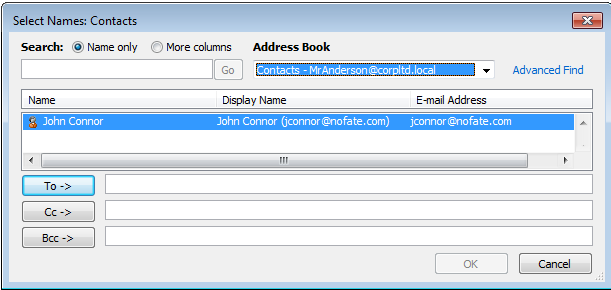
Cryptolocker's harvesting function was observed in a test environment running Microsoft SBS Server 2008 and Exchange 2007 together with a Windows 7, Outlook 2010 client. A sample GAL entry represents our victim:
This sample of Cryptolocker only appears to support 32-bit MAPI, since execution against 64-bit MAPI (i.e. 64-bit Outlook) results in the below error. This occurs at the initial call to MAPIInitialize. In this state Cryptolocker executes plan B, which is to harvest contacts from the local Windows Address Book using wab32.dll and the same code path (minus the calls to MAPIInitialise and MAPILogonEx).
The following table indicates if the Outlook harvesting function was successful based on the version of Windows and Outlook running at the time of execution:
With this information moved into the hands of ransomware operators, it's not unreasonable to assume it could be used to hone successive attacks. Sale of the information to other groups is also a way to boost revenue, by supplementing the income from ransom payments with the sale of stolen contact information. A 90,000+ entry GAL dump from Corp. Ltd may be of interest to affiliates operating with a different family of malware (e.g. the well-known Dyre banking trojan).










No comments:
Post a Comment